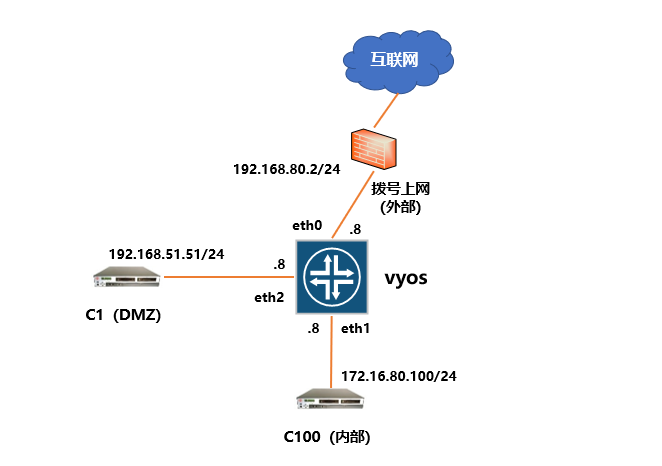
- 沿用上一篇VyOS基础操作的实验拓扑
VyOS接口的三个方向
同时也是 VyOS 接口防护的三个方向:
- in :进入该接口的流量,且数据包的目的地址不是接口自身地址;
- out: 流出该接口的流量,且数据包的源地址不是接口自身地址;
- local:该接口自身的地址。
VyOS防火墙策略
- VyOS 防火墙的每条策略都需要设置一个默认 action,这条规则最后匹配。
- 此外策略中的每条规则都对应一个 rule 值,按照 rule 值从小到大顺序匹配。
外部接口策略:
vyos@vyos# set firewall name Wan2Lan default-action drop # 默认action
vyos@vyos# set firewall name Wan2Lan rule 1 action accept
vyos@vyos# set firewall name Wan2Lan rule 1 state established enable
vyos@vyos# set firewall name Wan2Lan rule 1 state related enable
## 放行状态为established和related的连接,即这个连接是内网发起的,否则内网访问外网不通
DMZ区接口策略:
vyos@vyos# set firewall name DMZ_ACL default-action drop
vyos@vyos# set firewall name DMZ_ACL rule 1 action accept
vyos@vyos# set firewall name DMZ_ACL rule 1 destination address 172.16.80.0/24
vyos@vyos# set firewall name DMZ_ACL rule 1 state established enable
vyos@vyos# set firewall name DMZ_ACL rule 1 state new disable
vyos@vyos# set firewall name DMZ_ACL rule 1 state related enable
vyos@vyos# set firewall name DMZ_ACL rule 2 action accept
vyos@vyos# set firewall name DMZ_ACL rule 2 destination address 0.0.0.0/0
内部接口策略:
vyos@vyos# set firewall name Inside_ACL default-action drop
vyos@vyos# set firewall name Inside_ACL rule 1 action accept
vyos@vyos# set firewall name Inside_ACL rule 1 destination address 192.168.51.0/24
vyos@vyos# set firewall name Inside_ACL rule 1 destination port 21,22,23,80,443
vyos@vyos# set firewall name Inside_ACL rule 1 protocol tcp
vyos@vyos# set firewall name Inside_ACL rule 1 source address 172.16.80.100
vyos@vyos# set firewall name Inside_ACL rule 2 action accept
vyos@vyos# set firewall name Inside_ACL rule 2 destination address 192.168.52.0/24
vyos@vyos# set firewall name Inside_ACL rule 2 destination port 21,22,23,80,443
vyos@vyos# set firewall name Inside_ACL rule 2 protocol tcp
vyos@vyos# set firewall name Inside_ACL rule 2 source address 172.16.80.100
vyos@vyos# set firewall name Inside_ACL rule 3 action reject
vyos@vyos# set firewall name Inside_ACL rule 3 destination address 192.168.51.0/24
vyos@vyos# set firewall name Inside_ACL rule 3 source address 172.16.80.100
vyos@vyos# set firewall name Inside_ACL rule 4 action reject
vyos@vyos# set firewall name Inside_ACL rule 4 destination address 192.168.52.0/24
vyos@vyos# set firewall name Inside_ACL rule 4 source address 172.16.80.100
vyos@vyos# set firewall name Inside_ACL rule 1000 action accept
vyos@vyos# set firewall name Inside_ACL rule 1000 destination address 0.0.0.0/0
vyos@vyos# set firewall name Inside_ACL rule 1000 source address 172.16.0.0/16
防火墙全局策略:
vyos@vyos# set firewall all-ping enable
vyos@vyos# set firewall broadcast-ping enable
vyos@vyos# set firewall ip-src-route enable
vyos@vyos# set firewall syn-cookies enable
策略应用到接口:
vyos@vyos# set interfaces ethernet eth0 firewall in name Wan2Lan
vyos@vyos# set interfaces ethernet eth1 firewall in name Inside_ACL
vyos@vyos# set interfaces ethernet eth2 firewall in name DMZ_ACL
vyos@vyos# set interfaces ethernet eth3 firewall in name DMZ_ACL
VyOS 防火墙 group 的概念
- VyOS 防火墙中 group 是将一组相似属性的东西归结起来,供防火墙的 rule 去引用,group分为address-group,network-group,port-group。
例如内部接口策略的 rule 1-4 可做如下优化:
vyos@vyos# set firewall group network-group dmz_network network 192.168.51.0/24
vyos@vyos# set firewall group network-group dmz_network network 192.168.52.0/24
vyos@vyos# set firewall name Inside_ACL rule 1 action accept
vyos@vyos# set firewall name Inside_ACL rule 1 destination group network-group dmz_network
vyos@vyos# set firewall name Inside_ACL rule 1 destination port 21,22,23,80,443
vyos@vyos# set firewall name Inside_ACL rule 1 protocol tcp
vyos@vyos# set firewall name Inside_ACL rule 1 source address 172.16.80.100
vyos@vyos# set firewall name Inside_ACL rule 3 action reject
vyos@vyos# set firewall name Inside_ACL rule 3 destination group network-group dmz_network
vyos@vyos# set firewall name Inside_ACL rule 3 source address 172.16.80.100
2019-08-16 修复图片
本文由 SHIYL 创作,采用 知识共享署名4.0 国际许可协议进行许可
本站文章除注明转载/出处外,均为本站原创或翻译,转载前请务必署名
最后编辑时间为: Aug 18, 2019 at 08:44 pm
